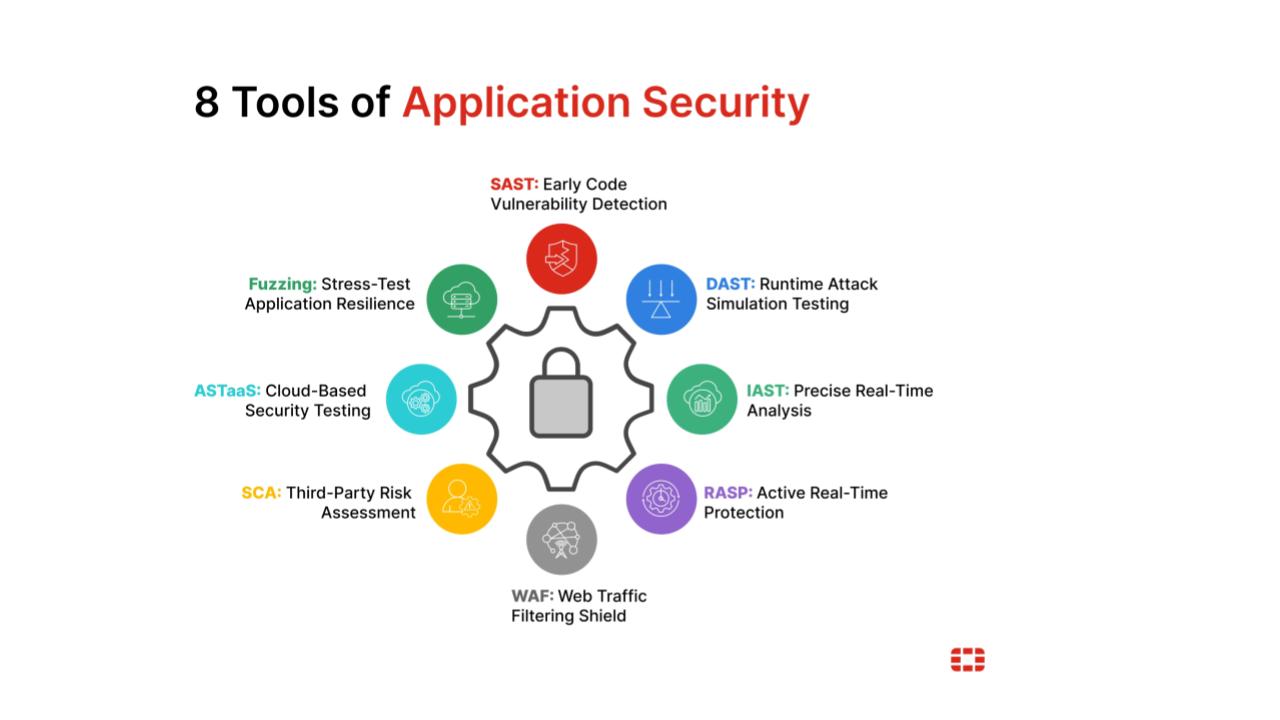
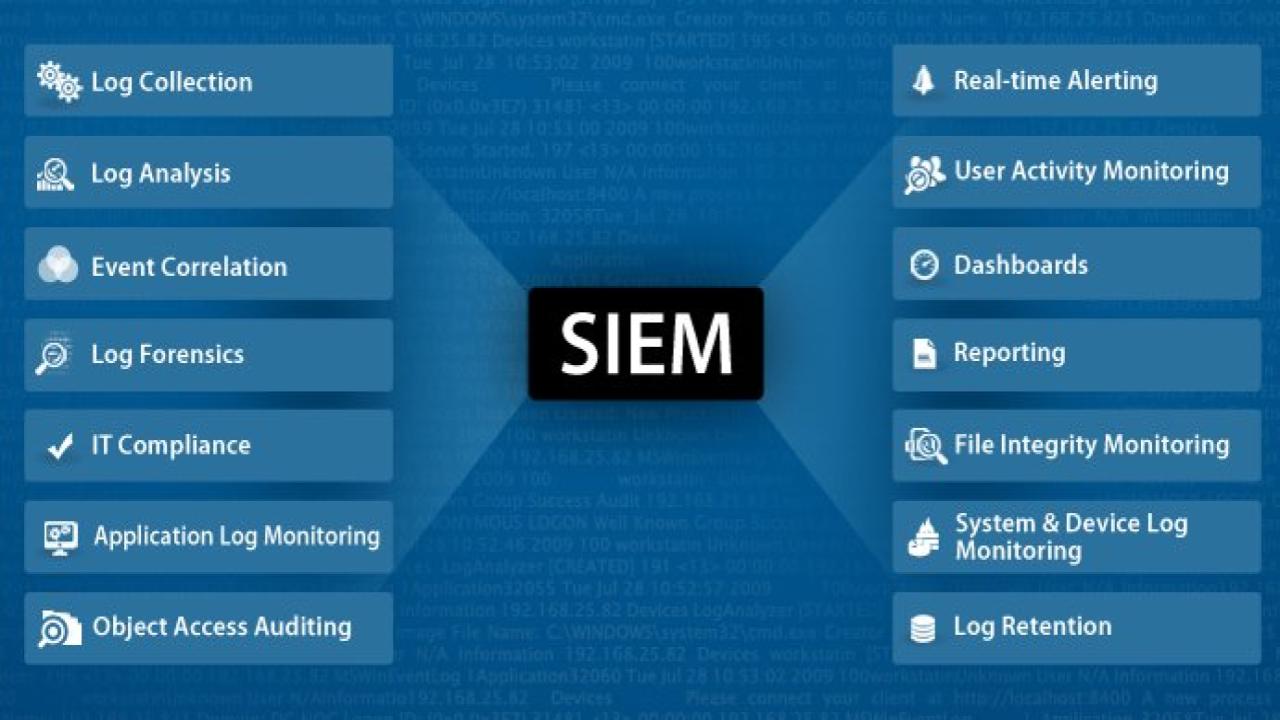
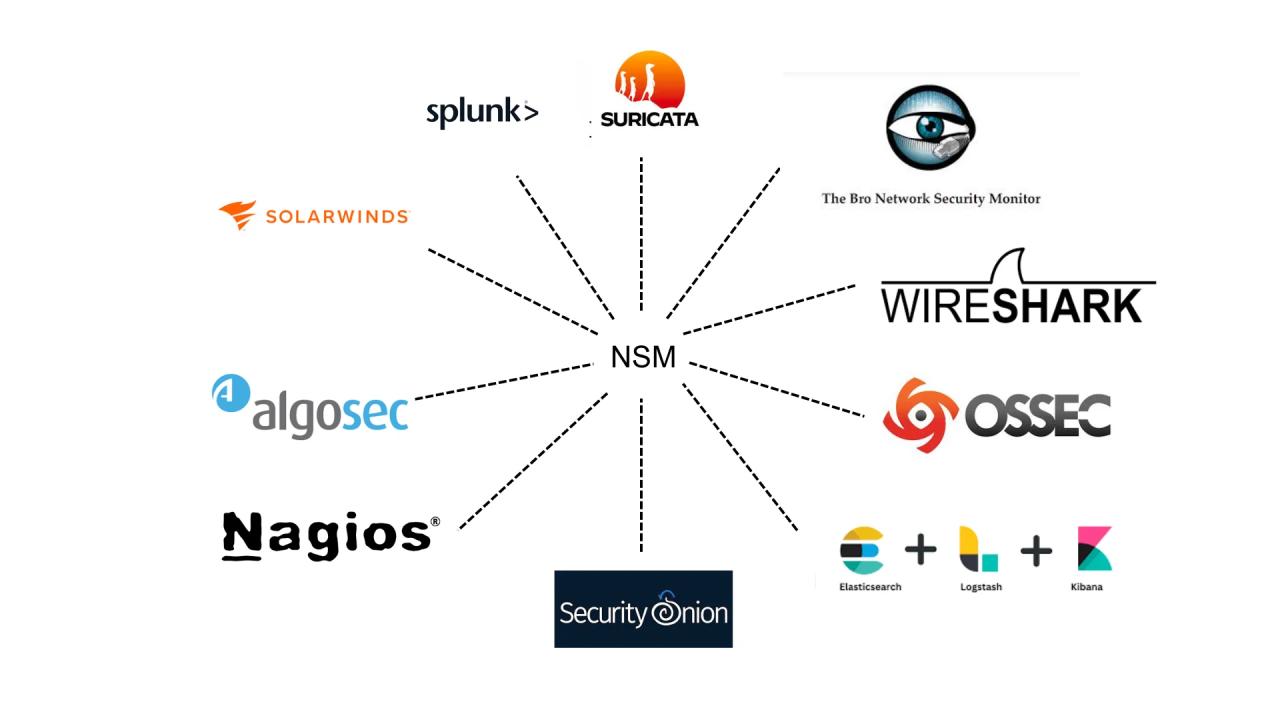
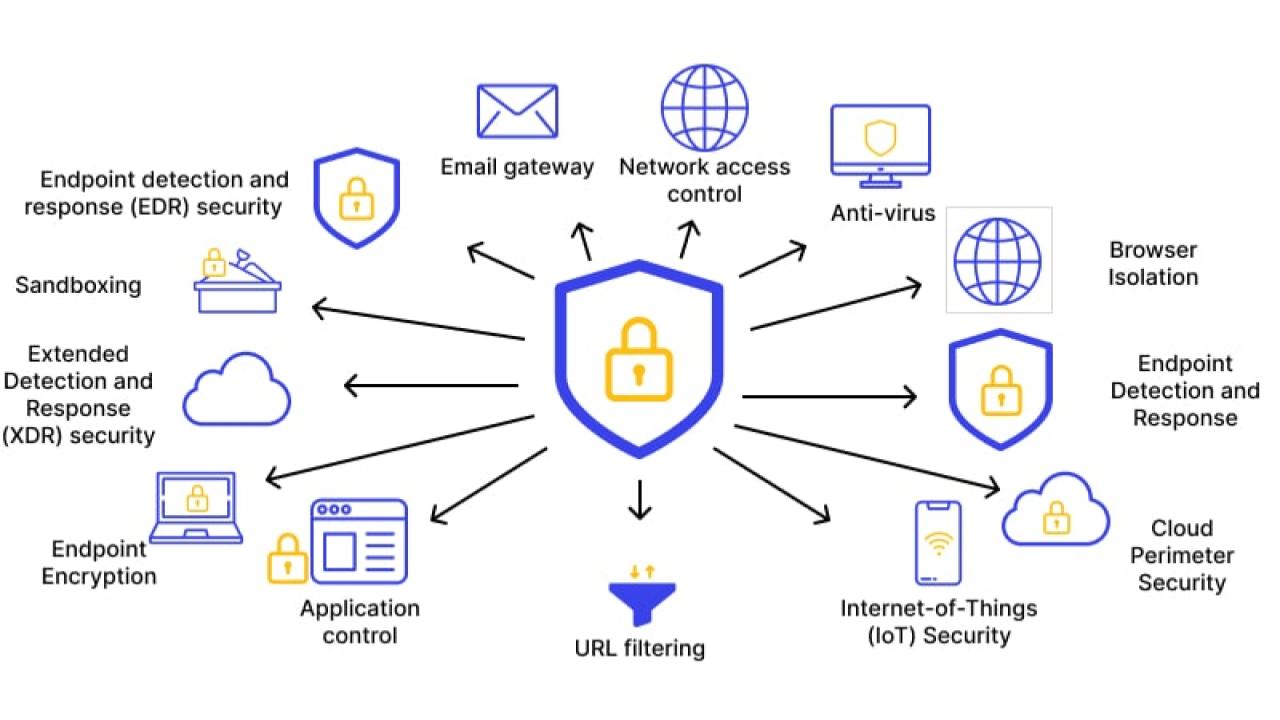
The top cybersecurity web application security tools include comprehensive platforms and specialized scanners, categorized by their testing methodology: Static (SAST), Dynamic (DAST), Interactive (IAST), and Software Composition Analysis (SCA).
Top web application security tools include Burp Suite and OWASP ZAP for comprehensive testing, Acunetix and Invicti (Netsparker) for automated vulnerability scanning, and Checkmarx for static code analysis. Other important tools are Nikto for web server scanning, sqlmap for SQL injection testing, and frameworks like Metasploit for penetration testing.
OnAir Post: Top Web Application Tools